Securely Connect Remote IoT VPC On AWS: Your Ultimate Guide
Alright, listen up, folks. If you're diving into the world of cloud computing and IoT, you're probably wondering how to securely connect remote IoT VPC on AWS without losing your mind. It’s not just about setting up connections; it’s about doing it right, ensuring everything stays secure, scalable, and efficient. In today’s fast-paced tech landscape, securing your IoT devices is more crucial than ever. So, buckle up, because we’re about to break it all down for you in simple terms.
Now, before we dive deep into the nitty-gritty of this topic, let’s address the elephant in the room. AWS is huge, and it can feel overwhelming at times. But don’t worry, we’re here to guide you through the process step by step. Whether you’re a seasoned pro or just starting out, this guide will help you understand how to create a secure environment for your IoT devices using AWS’s Virtual Private Cloud (VPC). Trust me, by the end of this, you’ll be a pro at setting up your remote IoT VPC securely.
One last thing before we get started. This isn’t just another tech article. We’re going to make sure you walk away with actionable insights and practical tips that you can implement right away. So, if you’re ready to take your IoT game to the next level, let’s jump in!
Table of Contents
- Introduction to AWS IoT and VPC
- Why Securely Connect Remote IoT VPC?
- Setting Up Your VPC
- Configuring Security Groups
- Using VPN for Remote Access
- Managing IAM Roles and Policies
- Best Practices for Security
- Troubleshooting Common Issues
- Scaling Your IoT Infrastructure
- Conclusion
Introduction to AWS IoT and VPC
Alright, let’s start with the basics. AWS IoT and VPC are two powerful tools that, when combined, can revolutionize how you manage your IoT infrastructure. AWS IoT allows you to connect, monitor, and manage billions of devices and thousands of applications. Meanwhile, VPC lets you create an isolated network environment where you can launch AWS resources in a virtual network that you define.
Now, when you’re dealing with remote IoT devices, having a secure connection is non-negotiable. That’s where VPC comes in. By setting up a VPC specifically for your IoT devices, you can ensure that they’re operating in a secure, isolated environment. This setup not only enhances security but also improves performance and reduces latency.
- Why Mkvmoviespoint Web Series Is Your Ultimate Bingewatching Destination
- Vegamoviesrs Your Ultimate Streaming Hub
Why Choose AWS for IoT?
Here’s the deal: AWS offers a ton of benefits for IoT setups. From its robust security features to its scalability and flexibility, AWS is the go-to platform for many enterprises. Plus, with AWS IoT Core, you can easily and securely connect devices to the cloud, enabling two-way communication between devices and the cloud.
Some key features of AWS IoT include:
- Device Gateway: Securely connects devices to AWS IoT Core.
- Rules Engine: Routes data to other AWS services.
- Device Shadow: Keeps track of device state even when the device is offline.
Why Securely Connect Remote IoT VPC?
Okay, so why all the fuss about securing your remote IoT VPC? Well, let’s face it, the internet of things is a double-edged sword. On one hand, it offers incredible opportunities for innovation and efficiency. On the other hand, it opens up a whole new world of security risks.
When you’re dealing with remote IoT devices, the last thing you want is for them to be compromised. A single breach could lead to sensitive data being exposed, devices being hijacked, or even entire networks being brought down. That’s why it’s essential to ensure that your IoT devices are securely connected to your VPC.
Key Security Concerns
Let’s break down some of the key security concerns when it comes to IoT:
- Data Privacy: Protecting sensitive data transmitted between devices and the cloud.
- Device Authentication: Ensuring that only authorized devices can connect to your network.
- Network Security: Preventing unauthorized access to your network.
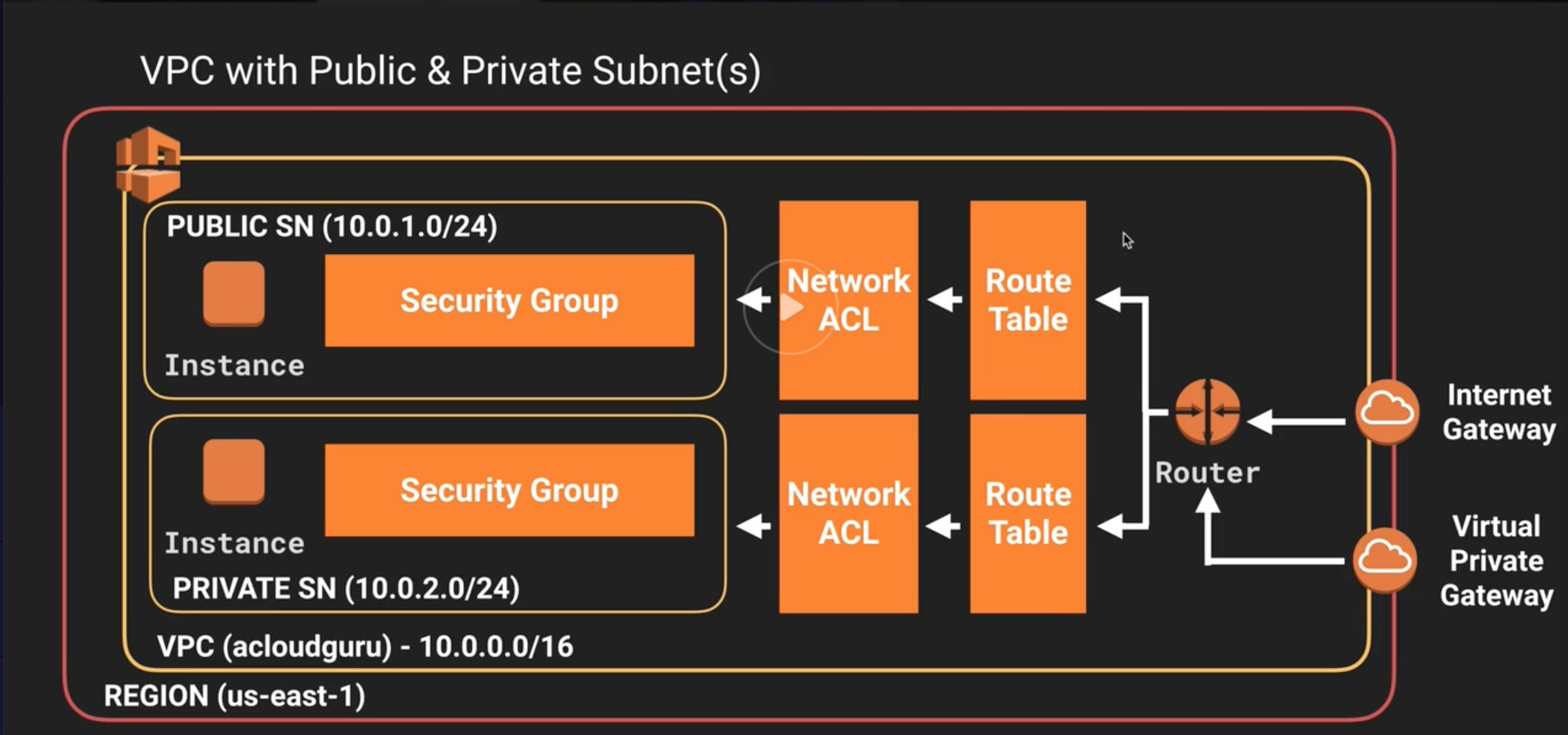
Setting Up Your VPC
Alright, now that we’ve covered the why, let’s talk about the how. Setting up a VPC for your IoT devices is a crucial step in ensuring their security. Here’s a quick rundown of the process:
First things first, log in to your AWS Management Console and navigate to the VPC dashboard. From there, you can create a new VPC by specifying the CIDR block, subnets, and other configurations. Make sure to set up public and private subnets to ensure that your devices have secure access to the internet while remaining isolated from the public network.
Key Steps in Setting Up a VPC
Here’s a step-by-step guide to setting up your VPC:
- Define your CIDR block.
- Create subnets for your public and private networks.
- Set up route tables to define how traffic flows within your VPC.
- Configure network ACLs to control inbound and outbound traffic.
Configuring Security Groups
Security groups are your first line of defense in AWS. Think of them as virtual firewalls that control inbound and outbound traffic to your instances. When setting up your IoT VPC, it’s crucial to configure security groups properly to ensure that only authorized traffic can access your devices.
Here’s how you can configure security groups:
- Create a security group for your IoT devices.
- Define inbound rules to allow only necessary traffic.
- Set up outbound rules to control what traffic leaves your instances.
Best Practices for Security Groups
Some best practices for configuring security groups include:
- Use least privilege: Only allow the minimum access required.
- Regularly review and update your security group rules.
- Monitor traffic to detect any suspicious activity.
Using VPN for Remote Access
Now, let’s talk about remote access. If you need to access your IoT devices from outside your VPC, setting up a VPN is a great option. AWS offers two types of VPN connections: Site-to-Site and Client VPN. Site-to-Site VPN is ideal for connecting your on-premises network to your VPC, while Client VPN allows individual users to securely access your VPC.
Setting up a VPN involves creating a virtual private gateway and configuring the necessary settings. Once set up, your remote devices can securely connect to your VPC, ensuring that all communication is encrypted and protected.
Benefits of Using VPN
Here are some benefits of using a VPN for remote access:
- Enhanced security through encryption.
- Seamless connectivity between on-premises and cloud environments.
- Easy management of remote access.
Managing IAM Roles and Policies
IAM (Identity and Access Management) is another critical component of securing your IoT VPC. By using IAM roles and policies, you can control who has access to your resources and what actions they can perform.
Here’s how you can manage IAM roles:
- Create IAM roles for different user groups.
- Attach policies to roles that define their permissions.
- Regularly review and update IAM policies to ensure they align with your security requirements.
Best Practices for IAM
Some best practices for managing IAM roles include:
- Use role-based access control (RBAC) to manage permissions.
- Avoid using root accounts for everyday tasks.
- Enable multi-factor authentication (MFA) for added security.
Best Practices for Security
Alright, let’s wrap up with some best practices for securing your remote IoT VPC. Here are a few tips to keep in mind:
- Regularly update your devices and software to patch vulnerabilities.
- Monitor your network for suspicious activity using AWS CloudTrail and AWS CloudWatch.
- Implement encryption for data at rest and in transit.
Troubleshooting Common Issues
Even with the best security measures in place, issues can still arise. Here are some common problems you might encounter and how to troubleshoot them:
- Connection Issues: Check your security groups and network ACLs.
- Performance Problems: Optimize your VPC settings and ensure proper scaling.
- Access Denials: Review your IAM policies and permissions.
Scaling Your IoT Infrastructure
Finally, let’s talk about scaling. As your IoT infrastructure grows, you’ll need to ensure that your VPC can handle the increased load. AWS offers several tools and services to help you scale your infrastructure, including Auto Scaling, Elastic Load Balancing, and AWS Lambda.
By leveraging these tools, you can ensure that your IoT devices remain performant and secure, no matter how much they grow.
Conclusion
And there you have it, folks. A comprehensive guide to securely connecting remote IoT VPC on AWS. By following the steps and best practices outlined in this article, you can ensure that your IoT devices are operating in a secure, scalable, and efficient environment.
Remember, securing your IoT infrastructure is an ongoing process. Stay vigilant, keep learning, and don’t hesitate to reach out if you have any questions or need further assistance. Now, it’s your turn to take action. Share this article, leave a comment, and let’s keep the conversation going!
Article Recommendations
- Hdhub4ucom Movie Your Ultimate Destination For Highquality Entertainment
- Jey Uso The Phenomenal Rise Of Wwes Dynamic Superstar


Detail Author:
- Name : Jena Runte
- Username : bert.jerde
- Email : dkub@muller.com
- Birthdate : 1997-06-03
- Address : 540 Zella Stream Port Sherwoodport, SC 90998
- Phone : (304) 554-1427
- Company : Kutch Group
- Job : Floral Designer
- Bio : Dolorem maxime architecto vero laborum. Accusantium dolorem quam libero et doloremque non iste. Qui aut odio non explicabo voluptatibus.
Socials
instagram:
- url : https://instagram.com/ramirobernhard
- username : ramirobernhard
- bio : Placeat aliquid sit et. Voluptas inventore hic quasi qui.
- followers : 3036
- following : 2412
tiktok:
- url : https://tiktok.com/@ramiro_id
- username : ramiro_id
- bio : Ut aut omnis fugit quis debitis iure. Tempore magni recusandae eum ut in.
- followers : 683
- following : 514
linkedin:
- url : https://linkedin.com/in/ramiro_dev
- username : ramiro_dev
- bio : Dolorem aliquid ipsum nemo eum voluptatem eum.
- followers : 2805
- following : 2012
twitter:
- url : https://twitter.com/ramiro_real
- username : ramiro_real
- bio : Dicta qui quasi similique id et voluptas. Eos est consequatur saepe nesciunt corporis. Nihil sed dolores maiores dolore sit maiores sed fuga.
- followers : 5831
- following : 1207
facebook:
- url : https://facebook.com/ramiro_bernhard
- username : ramiro_bernhard
- bio : Qui ut sint consequatur.
- followers : 4642
- following : 1245